Data Breach
Security Measures against Data Breaches
The organizational and technical measures mentioned in the Regulation are the cornerstone of the discipline: they concern both the most appropriately technical measures (such as authentication credentials, authorization profiling system, encryption, antivirus and back up etc.) and the organizational ones (such as contractual regulation of relationships with those data processors, confidentiality constraints and instructions given to individuals who work on data, policies and records of processing, etc.). One of the interaction profiles of organizational and technical measures with the security system is to protect and respond to personal data breaches.
The declination of organizational and technical measures in the information security system
Technical-organizational measures interact with the entire system for the protection of personal data under different profiles:
• As a system of protection and reaction to violations (data breach)
• As verification and demonstration of compliance (accountability)
• As a tool for reducing risk (minimizing data, pseudonymization, privacy by design)
• As a Risk Assessment Component (DPIA)
• As organizational measure (contractual constraints with processors, confidentiality of people managing data, policies and registers)
• As a way of faacilitating the exercise of rights (opposition, forgiveness or cancellation, limitation of processing, portability, profiling and automated decisions).
Prevention and reaction to data breaches
The security measures objectives – found in the Regulation – are dual:
• of an “active” or a preventative nature, consisting in reducing the risk of unauthorized destruction, loss, modification, disclosure or accidental or unlawful access to personal data
• of a “passive” or “reactive” nature, consisting in a prompt response to incidents in the implementation of effective remediation actions and timely communications to the competent authorities, data subjects and the Controller (if the incident concerns the Processor).
The criterion of adequacy of the measures
The “active” protection profile requires the adoption of an adequate security level. The determination of the adequacy of the level is achieved adopting a risk-based approach: «appropriate technical and organisational measures to ensure a level of security appropriate to the risk» should be implemented, «taking into account the state of the art, the costs of implementation and the nature, scope, context and purposes of processing as well as the risk of varying likelihood and severity for the rights and freedoms of natural persons» (Article 32 (1)).
The legislator provides an example list of such measures that may include:
• «(a) the pseudonymisation and encryption of personal data;
• (b) the ability to ensure the ongoing confidentiality, integrity, availability and resilience of processing systems and services;
• (c) the ability to restore the availability and access to personal data in a timely manner in the event of a physical or technical incident;
• (d) a process for regularly testing, assessing and evaluating the effectiveness of technical and organisational measures for ensuring the security of the processing.».
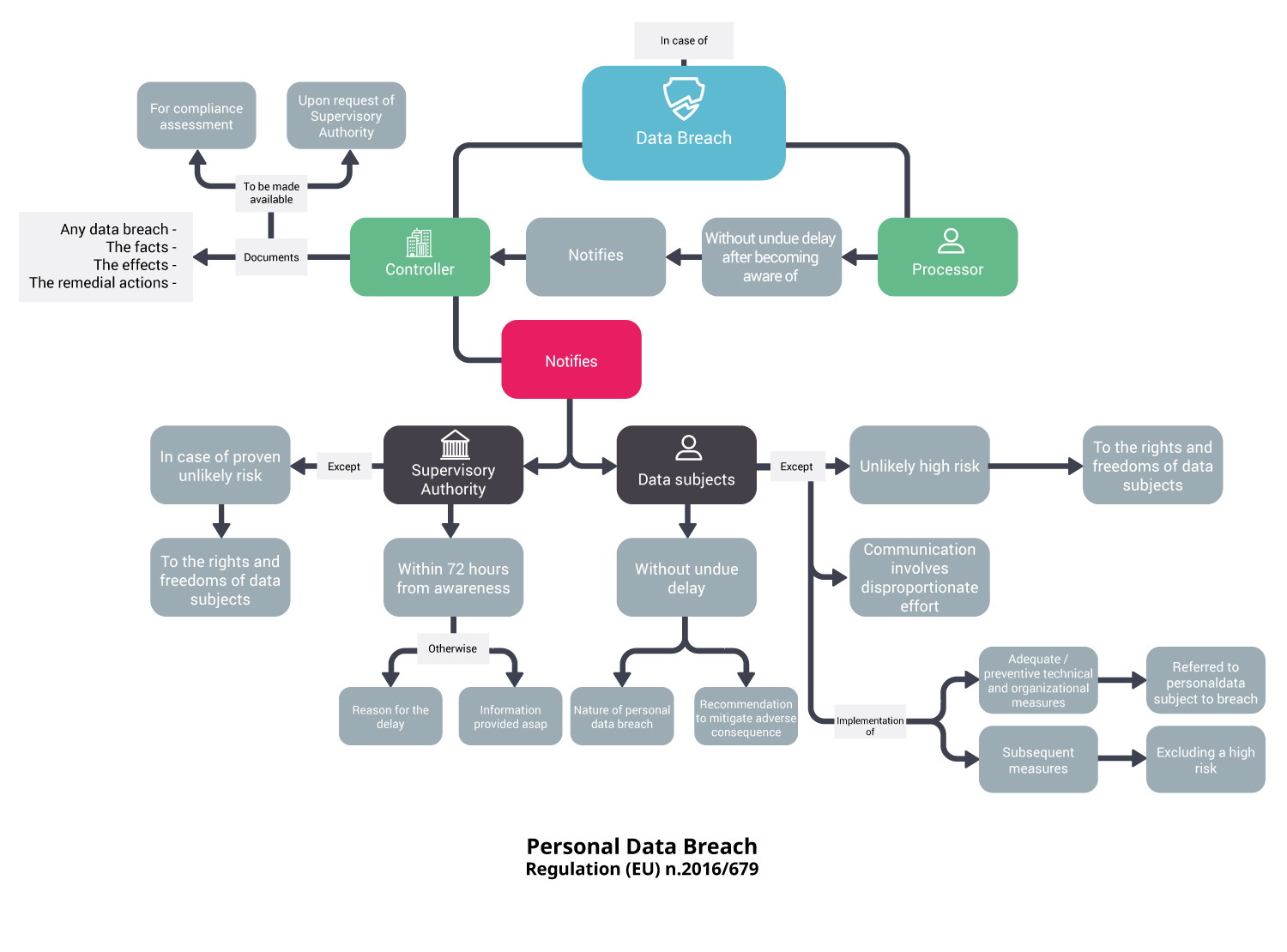
Data breach incidents
On the “reactive” front, in addition to system resilience and recovery policies, the legislator imposes specific disciplines in case of data breaches.
The state of the law
It should be noted that, according to EU Regulation no. 611/2013, concerning publicly available electronic communications providers, encryption or hashing systems are not considered to be comprehensive remedies for protection against the risk of infringement, as they must be accompanied by appropriate organizational and technical measures under art . 17 of Directive 95/46 [Recital (17)]. However, they allow – if they comply with the conditions laid down – to avoid notifying users in case of a breach (see Article 4).
Cybersecurity Directive
The so-called Cybersecurity Directive is being published on the Official Journal of the European Union. The Directive envisages for energy, transport, banking, financial market infrastructure, health and water supply services:
• the adoption of security measures to manage the risks to the networks and information systems that they control and use in their respective activities
• the notification to the competent authorities of those incidents having a significant impact on the continuity of the essential services they provide.
• These provisions should be harmonized with the corresponding ones contained in the Regulation on the processing of personal data.
GDPR
The Regulation extends the reporting obligations for personal data breaches to their respective competent authorities, to all Data Controllers. The notification must be made without unjustified delay and, in any case, within 72 hours of the date on which it has become known, unless the Controller demonstrates that it is unlikely that the data breach would present a risk to the rights and freedoms of the data subjects affected by the breach. If the notification takes place after the 72-hours deadline, the reasons for the delay must be explained [Recital (67) and art. 31]. In the event of a high risk for the rights and freedoms of the data subjects, notification should also be made to the latter, by making recommendations to mitigate potential adverse effects. Notification to data subjects must be carried out «as soon as reasonably feasible and in close cooperation with the supervisory authority, respecting guidance provided by it or by other relevant authorities such as law-enforcement authorities» [Recital (86)].
Adopting appropriate technical measures to effectively limit the risk of identity theft or other forms of abuse positively affects the consequences of a data breach and the resulting legal implications.
Personal Data Breach
Sanction for Sensitive Data Breach
Infringement related to the processing of sensitive data (Article 9) is sanctioned with administrative fines of «up to 20 000 000 EUR, or in the case of an undertaking, up to 4 % of the total worldwide annual turnover of the preceding financial year, whichever is higher» (Article 83.5).