Characterizing Services
Whether in designing a service-oriented system or in creating a reference pattern, service identification is a mandatory phase.
We can use the following typology to identify services:
• functional services
• services deduced from data models
• application services
• business process orchestration services
• technical and infrastructure services
These services can be deduced from analysis of enterprise business processes. Analysis of this business process results in a breakdown into operations executed by enterprise org-units (see the MEGA Process guide for more details). For each operation, it is possible to determine to what extent the operation needs to be equipped with an IT service facility. This then brings to light a set of services that are used when the process is carried out.
In the following example, the "Handle a real estate credit order" process is partially accomplished by the branch manager who implements the operation: “Study and give ruling on the credit request”. The realization of this operation is assisted by a functional service: “Summary of Client Situation”.
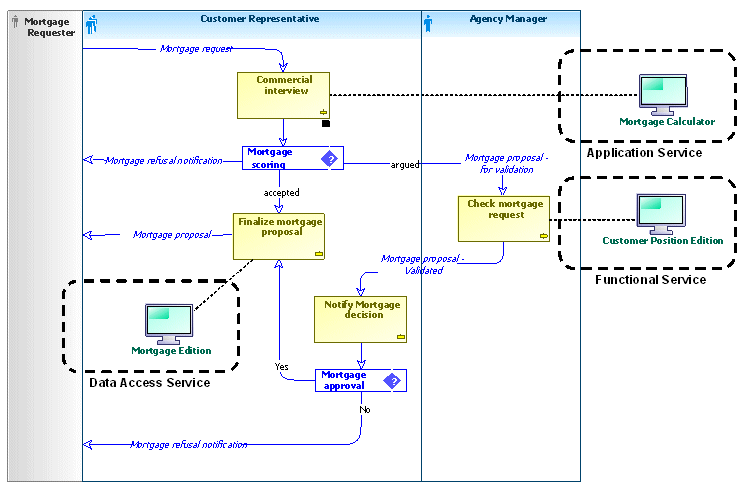
Example of the functional services of a process
Services deduced from data models
The data used in the context of enterprise processes also constitute indicators for service detection. In the above example, the operation: “Finalizing the credit proposal” illustrates the need to have one or more management services for the “Credit offering” entity. The credit is itself linked to the client entity whose properties need to be consulted.
The read, update, creation and deletion services for each of these entities can thus be defined. These four basic services are generally referenced by the acronym CRUD (Create, Retrieve, Update, Delete) and most often result in implementation in a relational database. From these core services are also derived the man-machine services that implement them.
Application services
Application services encapsulate algorithms for carrying out complex calculations or implementing business rules. In the credit example, a mortgage simulation service is used in the client interview. This service implements centralized computation algorithms and may be shared by other processes.
Business process orchestration services
Process orchestration services allow the chaining of the tasks implemented by the elementary services with the goal of automating all or part of the business process value chain.
For example, a flight booking system handles customer standby in the event of a flight being full. As soon as someone cancels, the service managing the process automatically handles the client call-back (sending an e-mail) and makes the booking. In this instance, the service manages the current status of the booking transaction (pending, reserved, canceled) for a period that may extend from several hours to several weeks.
Process execution engines available on the market (BPMS: Business Process Management System), are based on the formal description of the processes using a language. The most popular of these languages is BPEL (Business Process Execution Language). There is also a graphical notation to represent these business process definitions: BPMN (Business Process Modeling Notation).
See the MEGA System Blueprint guide for more details.
Communication services
A Service Oriented Architecture is based on services and their interactions. Interaction management itself gives rise to the implementation of dedicated services. In an architecture of this type, it is essential to use protocols and standard services able to transmit messages between the various business function services. Since the services are of mixed type, the communication system is based on protocols that are independent of the messages transferred. It is therefore necessary to have services dedicated to "translation" of messages from their native format to independent format, and vice versa.
SOAP is a good example of a protocol used to address this issue. There are a large number of services that are capable of handling or transferring a SOAP message, whether this be on Unix, Windows or any other platform.
Administration services
The IT system is one of the main levers in process implementation. As such, it requires administration that allows decisions to be made in relation to its evolution. It is therefore a good idea to define a specific architecture for the administration of the IT system. The objective is generally to determine:
• if all the services implemented cater to requirements
• if they are correctly dimensioned for a performance viewpoint
• if they are continually accessible
• if they are regularly and easily updated, etc.
To address these internal issues, we may have recourse to the services defined below (this list is not exhaustive):
• Incident logging service;
• Network traffic analysis services
• Application update services
• Security administration services
• Material resource identification services, etc.
Security services
As for administration, the notion of security for the IT system may be considered beyond the functional implications. It is an entirely discrete issue which cuts across every service layer, whatever the business function involved Here, the objective is to protect the IT system against all kinds of attack, whether via software or hardware, and whether intentional or not.
Among the services corresponding to this problem we find:
• Access services: the objective is to control access to applications, servers or certain parts of the network. Firewall applications are dedicated to this problem.
• Authentication services: this involves checking the identity of persons trying to access software resources. Protocols such as SSO (Single Sign On) allow unified authentication for several applications used on the same workstation.
• Integrity services: the purpose is to guarantee that the transmitted data have not been altered during their transit. These services are generally based on calculating a key, whose value depends on the transferred content. On arrival, the key and content are compared to detect any integrity breach.
• Confidentiality services: this involves checking that the data transferred to one person may not be read by another. Encryption services are generally the solution here.
A number of organizations have taken on the duty of inventorying possible security risks in order to deal with them better. Among these we find ITIL (Information Technology Infrastructure Library) and CERT (Computer Emergency Response Team) recommendations .
Identifying interactions
Interaction identification is carried out at the same time as service identification. Identifying a service allows you to identify the interactions that are associated with that service . For example, on the basis of a service called Credit simulator it is possible to identify an incoming message: "Request for credit simulation" and an outgoing message: "Credit simulation".
This example shows that one message alone is not enough to represent all the interactions necessary to obtain a result. To do this, it is necessary to group these messages within an interaction.
An interaction is an exchange contract between two or more partners. Each partner is represented by the role it plays in the exchange contract. Each elementary interaction in the protocol is specified by a message.
Interactions make it possible to describe the service interfaces, i.e.: all the input and output messages that they need to take into account. In our example, the Mortgage Simulation interaction comprises the two messages: Mortgage Simulation Request and Mortgage Simulation.
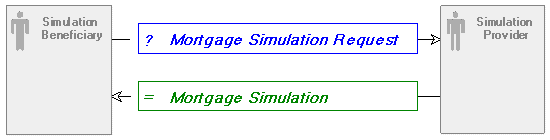
Interaction example
The "Mortgage Calculator" application offers a "Mortgage Simulator" capability. This plays the role of "Simulation Supplier". It must therefore reply to the "Credit Simulation Request" message with the "Credit simulation" message. The "Credit Simulation" internal application diagram shows how the "Credit Simulator" service is called via the "Credit Simulation" interaction. This same service must itself collaborate with the "Client Situation Consultation" and "Real Estate Risks Assessment" services to be able to carry out its processing.
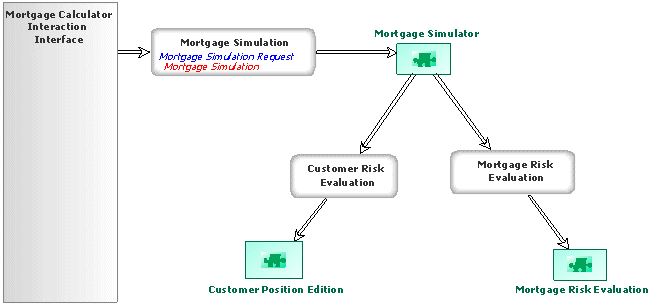
Example of collaborating services – Credit simulation application